In an era where our lives are intertwined with the internet, the need to protect our digital spaces has never been more urgent. From online banking to remote work, every click and connection exposes us to potential cyber threats like hackers, malware, and data breaches. This is where firewalls come into play—acting as the unsung heroes of network security.
Imagine a firewall as a digital bouncer, standing guard at the entrance of your network, deciding who gets in and who stays out. But what exactly is a firewall, and how does it keep your data safe? In this article, we’ll unpack the essentials of firewalls, exploring their types, mechanics, and critical role in defending both personal and professional networks. Whether you’re a curious beginner or a tech-savvy reader, understanding firewalls will empower you to navigate today’s cybersecurity landscape with confidence.
On This Page
Table of Contents
1. What Is a Firewall? Defining the Basics
A firewall is a security tool—either hardware, software, or a combination of both—designed to monitor and control network traffic based on predefined rules. Think of it as a filter that sits between your network and the outside world, blocking unauthorized access while allowing safe data to pass through. The term “firewall” originates from the physical barriers used to stop fires from spreading in buildings—a fitting analogy for its role in containing digital threats.
- Purpose: Protect networks from unauthorized access, malware, and other malicious activities.
- Example: When you visit a website, your firewall checks if the connection is safe before letting data flow to your device.
For instance, if a hacker tries to sneak into your home Wi-Fi to steal your passwords, a properly configured firewall can detect and block that attempt, keeping your sensitive information secure.
2. Types of Firewalls: From Hardware to Software
Not all firewalls are created equal—they come in various forms, each suited to specific needs. Here’s a breakdown:
| Type | Description | Best For | Example |
|---|---|---|---|
| Hardware Firewall | Physical devices placed between your network and the internet. | Businesses, large networks | Cisco ASA firewall appliance |
| Software Firewall | Programs installed on individual devices to filter traffic. | Personal computers, laptops | Windows Defender Firewall |
| Cloud-Based Firewall | Virtual firewalls hosted in the cloud, offering scalability and flexibility. | Remote teams, small businesses | AWS Network Firewall |
| Next-Generation Firewall (NGFW) | Advanced firewalls with added features like intrusion detection. | Enterprises | Palo Alto Networks NGFW |
- Hardware Example: A small business uses a hardware firewall to protect its office network from external attacks.
- Software Example: Your laptop’s built-in firewall blocks a suspicious app from sending data to an unknown server.
- Cloud Example: A startup with remote employees uses a cloud-based firewall to secure connections across multiple locations.
Each type has its strengths, and choosing the right one depends on your network size, budget, and security needs.
3. How Firewalls Work: The Mechanics of Protection
So, how does a firewall actually keep your network safe? It operates by analyzing network traffic—the data packets traveling to and from your device—and applying security rules. Here’s a step-by-step look:
- Packet Filtering: Examines data packets (small chunks of information) based on rules like IP addresses, ports, or protocols.
- Example: Blocks traffic from a known malicious IP address.
- Stateful Inspection: Tracks the “state” of connections (e.g., whether a packet is part of an established session).
- Example: Allows a reply from a website you visited but blocks unsolicited incoming data.
- Proxy Service: Acts as an intermediary, hiding your device’s identity from external servers.
- Example: A proxy firewall masks your IP when browsing, adding privacy.
Picture this: You’re streaming a movie. The firewall checks each packet of video data, ensuring it’s from a trusted source like Netflix and not a hacker’s server. If anything looks fishy, it’s dropped instantly.
4. Key Features of Modern Firewalls
Today’s firewalls go beyond basic filtering. They’re packed with advanced tools to tackle sophisticated threats. Here are some standout features:
- Intrusion Prevention System (IPS): Detects and stops attacks in real-time.
- Example: Blocks a ransomware attempt before it encrypts your files.
- Deep Packet Inspection (DPI): Looks inside data packets for hidden threats, not just their headers.
- Example: Spots malware disguised as a legitimate file download.
- Virtual Private Network (VPN) Support: Encrypts your connection for secure remote access.
- Example: Protects your data when using public Wi-Fi at a coffee shop.
- Application Control: Manages which apps can access the network.
- Example: Blocks social media apps during work hours on a company network.
These features make modern firewalls versatile guardians, adapting to the evolving cyber threat landscape.
5. Firewalls vs Cyber Threats: What They Can (and Can’t) Stop
Firewalls are powerful, but they’re not invincible. Let’s explore their strengths and limitations.
What Firewalls Can Stop
- Malware: Prevents malicious software from entering via network traffic.
- Example: Blocks a Trojan horse hiding in an email attachment.
- Distributed Denial of Service (DDoS) Attacks: Limits overwhelming traffic meant to crash your network.
- Example: Filters out fake requests flooding a small business website.
- Unauthorized Access: Stops hackers from sneaking into your system.
- Example: Denies entry to someone trying to guess your router’s password.
What Firewalls Can’t Stop
- Insider Threats: If a trusted user misuses access, a firewall won’t help.
- Example: An employee downloading sensitive data to a USB drive.
- Social Engineering: Can’t prevent you from clicking a phishing link.
- Example: You unknowingly give your password to a fake login page.
- Encrypted Threats: Struggles with malware hidden in encrypted traffic unless equipped with DPI.
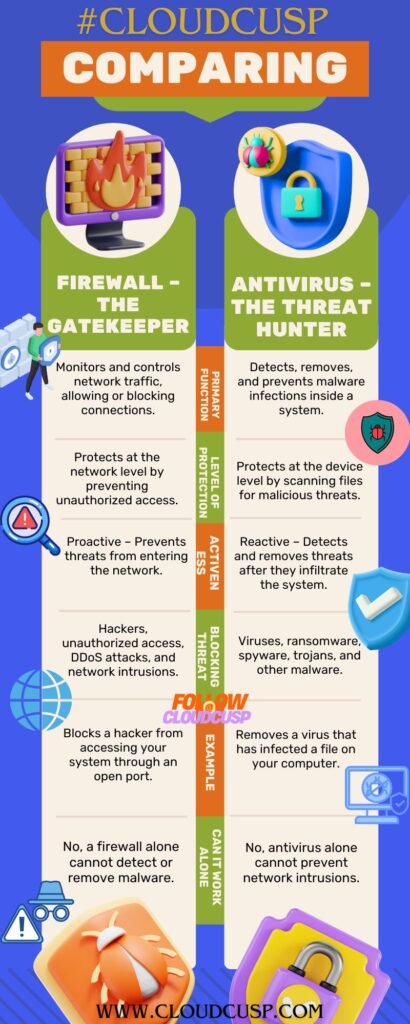
A firewall is a critical layer of defense, but it works best alongside antivirus software, user education, and other security measures.
6. Setting Up a Firewall: Best Practices for Implementation
Installing a firewall is just the beginning—proper setup is key to its effectiveness. Here’s how to do it right:
- Define Clear Rules: Specify what traffic to allow or block.
- Example: Allow port 80 for web browsing but block port 23 (Telnet) to prevent vulnerabilities.
- Update Regularly: Keep firmware and software patched against new threats.
- Example: A recent update fixes a flaw hackers could exploit in your router’s firewall.
- Monitor Logs: Check firewall activity to spot unusual patterns.
- Example: Notice repeated login attempts from an unknown IP and block it.
- Test Your Setup: Simulate attacks to ensure your firewall holds up.
- Example: Use a tool like Nessus to test for weak spots.
- Limit Access: Restrict who can change firewall settings.
- Example: Only the IT admin, not every employee, can tweak rules.
For a home user, enabling the default firewall on your router and adding a software firewall on your PC is a solid start. Businesses might invest in a next-generation firewall with professional oversight.
7. Firewalls Evolution with Technology
As cyber threats grow smarter, firewalls are evolving too. Here’s what’s on the horizon:
- AI-Driven Firewalls: Use machine learning to predict and block threats proactively.
- Example: An AI firewall flags a new type of malware before it’s officially identified.
- Zero-Trust Architecture: Assumes no user or device is trustworthy until verified.
- Example: Even an employee’s laptop must authenticate every time it connects.
- Integration with IoT: Protects the growing number of smart devices (e.g., thermostats, cameras).
- Example: Blocks a hacked smart fridge from joining a botnet.
- Cloud-Native Solutions: Scales with cloud-based workloads.
- Example: Secures a company’s data spread across Google Cloud and Azure.
The future promises firewalls that are faster, smarter, and more adaptive—essential as we rely more on digital systems.
WrapUP
In a world where cyber threats loom large, firewalls remain steadfast protectors of our networks. They filter out dangers, enforce boundaries, and provide peace of mind in an unpredictable digital age. From blocking malware to shielding against DDoS attacks, their role is foundational—yet they’re not a standalone solution. Pairing a firewall with good habits, like avoiding phishing scams, and complementary tools, like antivirus software, creates a robust defense.
As technology marches forward, so do firewalls, adapting with innovations like AI and zero-trust models. Whether you’re securing a single device at home or an enterprise network spanning the globe, a well-deployed firewall is your trusty companion in the ongoing battle for a safer, more secure digital future.

FAQs
What’s a firewall in simple terms?
A firewall is like a security guard for your internet connection. It checks the data coming in and out of your network—like emails, websites, or files—and decides what’s safe to let through and what to block based on rules you set.
Do I really need a firewall?
Yes! Without one, your computer or network is an open door for hackers, viruses, or anyone trying to mess with your stuff. It’s like locking your house—you wouldn’t leave it wide open, right?
Is the firewall on my computer enough?
It’s a good start, but it might not catch everything. The firewall on your computer (like Windows Defender) protects that one device. Adding a firewall on your router or using a fancier one can protect your whole home or office network better.
Can a firewall stop all hackers?
Not always. It’s great at blocking sneaky outsiders, like someone trying to break in through your Wi-Fi. But if you accidentally click a bad link or give away your password, a firewall can’t stop that—it’s not a mind reader!
What’s the difference between a hardware and software firewall?
A hardware firewall is a physical box, like a gadget you plug into your network (e.g., in a router). A software firewall is a program on your computer or phone. Hardware protects everything connected to it; software just protects that one device.
How do I know if my firewall is working?
You can check its settings—like on your router or computer—to see if it’s turned on. Some let you look at logs (a list of what it’s blocked). Or, try a free online test, like ShieldsUP, to see if it’s keeping things safe.
Can a firewall slow down my internet?
Sometimes, but not much. It’s busy checking data, so if it’s super strict or old, you might notice a tiny lag. Modern firewalls, especially fast ones, usually don’t mess with your speed.
Do I need to update my firewall?
Yep! Just like your phone needs updates, firewalls get new “instructions” to fight the latest tricks hackers use. If it’s outdated, it’s like using an old lock that everyone knows how to pick.
What’s a “next-generation” firewall?
It’s a souped-up version of a regular firewall. Besides blocking bad traffic, it can spot sneaky attacks, check inside data for hidden threats, or even let you use a VPN for extra safety. Think of it as a smart security guard with binoculars.
Can a firewall protect my smart TV or fridge?
It can help! If they’re on your network, a firewall (like one in your router) can stop hackers from taking over your smart gadgets. But you’ll need to make sure it’s set up to watch those devices too.









