Encryption is the art of protecting information by transforming it into an unreadable format. Throughout history, people have sought ways to keep their secrets safe from prying eyes. Let’s explore the fascinating journey of encryption, from its early methods to its modern-day applications. 🕵️♂️🔒
On This Page
Table of Contents
Early Encryption Solutions/Methods
One of the earliest forms of encryption was the Caesar Cipher, used by Julius Caesar himself. This method involved shifting the letters of the alphabet by a fixed number of places. For example, shifting the alphabet by three places would turn ‘A’ into ‘D’, ‘B’ into ‘E’, and so on.

Here’s a quick example:
| Original | Shifted |
|---|---|
| HELLO | KHOOR |

Another historical method is the Enigma machine used during World War II. This complex device used a series of rotating wheels to create encrypted messages that were incredibly difficult to decipher without the correct settings.
Evolution of Cryptography
As technology advanced, so did the methods of encryption. The advent of computers allowed for more complex algorithms and stronger encryption solutions. Modern cryptography relies on mathematical principles and algorithms to create secure communication channels.
Some common real-life applications of encryption today include:
- Online Banking: Protecting your financial information during transactions.
- Messaging Apps: Ensuring private conversations through end-to-end encryption.
- Secure Websites: Using HTTPS to encrypt data between your browser and the website.

What is Encryption? 🔒

Encryption is a method used to protect our data by converting it into a code that only authorized users can decipher. Think of it as a secret language only you and your best friend understand. This is essential in today’s digital world to keep our personal and sensitive information safe from prying eyes.
Symmetric vs. Asymmetric Encryption ⚖️
There are two main types of encryption: symmetric and asymmetric.
Below is a table summarizing the pros and cons of each type of encryption:
| Type | Pros | Cons |
|---|---|---|
| Symmetric Encryption | Fast, Efficient for large data volumes | Key distribution challenges, Single key for encryption and decryption |
| Asymmetric Encryption | Enhanced security, No need for shared key | Slower, Less efficient for large data volumes |
Here’s a quick comparison:
| Symmetric Encryption | Asymmetric Encryption |
|---|---|
| 🔑 Uses the same key for both encryption and decryption. | 🔑 Uses a pair of keys – a public key for encryption and a private key for decryption. |
| ⚡ Faster and more efficient. | 🛡️ More secure but slower. |
| 🔐 Commonly used for encrypting large amounts of data. | 🔐 Often used for secure communications, like emails. |
To illustrate the difference, consider a simple coding example. In symmetric encryption, the same key might be used as follows:
# Symmetric Encryption Example
from Crypto.Cipher import AES
key = b'Sixteen byte key'
cipher = AES.new(key, AES.MODE_EAX)
nonce = cipher.nonce
ciphertext, tag = cipher.encrypt_and_digest(b'Encrypt this message')
For asymmetric encryption, two keys are used:
# Asymmetric Encryption Example
from Crypto.PublicKey import RSA
from Crypto.Cipher import PKCS1_OAEP
# Generate keys
key = RSA.generate(2048)
public_key = key.publickey()
private_key = key
# Encrypt with public key
cipher = PKCS1_OAEP.new(public_key)
ciphertext = cipher.encrypt(b'Encrypt this message')
# Decrypt with private key
decipher = PKCS1_OAEP.new(private_key)
plaintext = decipher.decrypt(ciphertext)
Encryption Keys and Algorithms 🗝️
Keys and algorithms are crucial components of encryption:
- Encryption Keys: These are like passwords that help lock and unlock the encrypted data. The strength of encryption largely depends on the length and complexity of the key.
- Algorithms: Algorithms are the mathematical formulas used to transform data into an encrypted format. Popular encryption algorithms include AES (Advanced Encryption Standard) and RSA (Rivest-Shamir-Adleman).
Symmetric Encryption
Encryption is like sending a secret message that only the intended recipient can read. Symmetric encryption is one of the simplest methods where the same key is used to both encrypt and decrypt the information. 📬🔑
Common Symmetric Encryption Solutions/Techniques
There are several symmetric encryption solutions/techniques, each with its own unique features. Here are a few popular ones:
| Technique | Details |
|---|---|
| DES (Data Encryption Standard) | One of the earliest encryption standards. It’s now considered outdated but was revolutionary in its time. |
| AES (Advanced Encryption Standard) | The most widely used encryption standard today, known for its security and efficiency. Commonly used in applications like WhatsApp and other messaging apps. 📲 |
| Blowfish | A flexible encryption method designed for fast performance. It’s often found in software for securing passwords. |
| Twofish | An advanced version of Blowfish, providing even stronger security. It’s used in a variety of applications, including file encryption tools. |
Real-Life Examples of Symmetric Encryption
Wondering where you might encounter symmetric encryption in your daily life? Here are some examples:


- Messaging Apps: Apps like WhatsApp use AES to ensure that only the intended recipient can read your messages. 📱
- File Storage: Tools like WinZip use symmetric encryption to protect files on your computer. 💾
- Online Banking: Banks use symmetric encryption to secure transactions, ensuring your financial information stays private. 🏦
Symmetric encryption solutions/techniques are essential in keeping our digital lives secure. From chatting with friends to banking online, these methods ensure our information stays private and protected.
Asymmetric Encryption🤔
Asymmetric encryption is a type of encryption where two different keys are used: one for encryption and another for decryption. It’s like having a locked mailbox where anyone can put letters in, but only the owner with the key can take them out. This technique ensures secure communication over the internet. Let’s break it down into simpler terms with some well-known examples!
Popular Asymmetric Encryption Solutions/Techniques 🔐
There are several asymmetric encryption methods, each with its own strengths. Here are the most common ones:
| Technique | Full Name | Brief Description |
|---|---|---|
| RSA | Rivest-Shamir-Adleman | A widely-used encryption standard that provides strong security. |
| ECC | Elliptic Curve Cryptography | Uses elliptic curves to provide the same security as RSA, but with smaller keys. |
| DSA | Digital Signature Algorithm | Used for digital signatures, ensuring the authenticity of digital messages. |
Real-Life Examples 🌐
Asymmetric encryption is all around us! Here are some examples:
- Online Shopping: When you buy something online, your payment information is encrypted using asymmetric encryption to keep it secure.
- Email Security: Services like Gmail use asymmetric encryption to protect your emails from prying eyes.
- Secure Messaging Apps: Apps like WhatsApp and Signal use asymmetric encryption to ensure that only you and the person you’re communicating with can read your messages.

Why Use Asymmetric Encryption? 🤷♂️
Asymmetric encryption is essential for secure communication because:
- Confidentiality: Ensures that only the intended recipient can read the message.
- Integrity: Confirms that the message has not been altered during transit.
- Authentication: Verifies the identity of the sender, ensuring they are who they claim to be.
In summary, asymmetric encryption is like a digital handshake that keeps our online interactions private and secure. It’s an invisible guardian of our digital world! 🛡️
Hash Functions and Their Role in Encryption
Hash functions are like the secret sauce in encryption! They take an input, which can be anything from text to an entire file, and return a fixed-size string of characters. This unique string is called a hash value or a digest. Think of it as a digital fingerprint! 🕵️♂️
Popular Hash Functions
There are several popular hash functions, each with its own strengths:
- MD5 (Message Digest Algorithm 5): An older algorithm that’s fast but has known vulnerabilities.
- SHA (Secure Hash Algorithms): A family of algorithms like SHA-1, SHA-256, and SHA-3, which are more secure and widely used today.
Real-Life Examples
Let’s look at how hash functions are used in our daily lives:

- Password Storage: When you create an account, your password is hashed before it’s stored. Even if someone accesses the database, they can’t see your actual password!
- Data Integrity: Hash functions ensure files haven’t been tampered with. When you download software, a hash value is often provided to verify the file’s integrity.
- Blockchain: Hash functions are the backbone of blockchain technology, ensuring data blocks are secure and linked.
Let’s see a simple example in Python using SHA-256:
import hashlib
message = "Hello, World!"
hash_object = hashlib.sha256(message.encode())
hex_dig = hash_object.hexdigest()
print(hex_dig)
This code will produce a unique SHA-256 hash for the message “Hello, World!” 🖥️
Hash Function Characteristics
Here are some key characteristics that make hash functions so powerful:
| Characteristic | Description |
|---|---|
| Deterministic | Same input always produces the same hash. |
| Fast Computation | Hash values are generated quickly. |
| Pre-Image Resistance | It’s hard to reverse-engineer the original input from the hash. |
| Collision Resistance | Two different inputs won’t produce the same hash. |
Hash functions are essential for modern encryption and data security. From safeguarding passwords to verifying data integrity, they play a crucial role in keeping our digital world secure. Next time you log in to an account or download a file, remember the humble hash function working behind the scenes! 🔐✨
Encryption in Modern Applications
Data encryption is a critical component in securing modern applications, ensuring that information remains protected whether it is stored or being transmitted.
SSL/TLS for Secure Web Communications

SSL (Secure Sockets Layer) and TLS (Transport Layer Security) are essential protocols for securing web communications, ensuring that data transmitted between a user’s browser and a web server is encrypted and protected. These protocols work by establishing an encrypted link, preventing unauthorized access and ensuring data integrity during transmission.
The process begins with a “handshake” between the browser and the server. During this handshake, both parties exchange cryptographic keys and agree upon encryption methods. This ensures that any data transferred after this point is encrypted and can only be decrypted by the intended recipient. The encryption ensures that even if the data is intercepted, it cannot be read without the proper decryption key.
Below is a simple comparison of SSL and TLS:
| Feature | SSL | TLS |
|---|---|---|
| Protocol Versions | SSL 2.0, SSL 3.0 | TLS 1.0, 1.1, 1.2, 1.3 |
| Security Level | Less Secure | More Secure |
| Performance | Slower | Faster |
| Use Cases | Legacy Systems | Modern Systems |
An example of SSL/TLS implementation is in online banking websites. These websites use SSL/TLS to encrypt sensitive information such as login credentials, transaction details, and personal data. This ensures that even if the data is intercepted, it remains unreadable to unauthorized parties.
End-to-End Encryption in Messaging Apps
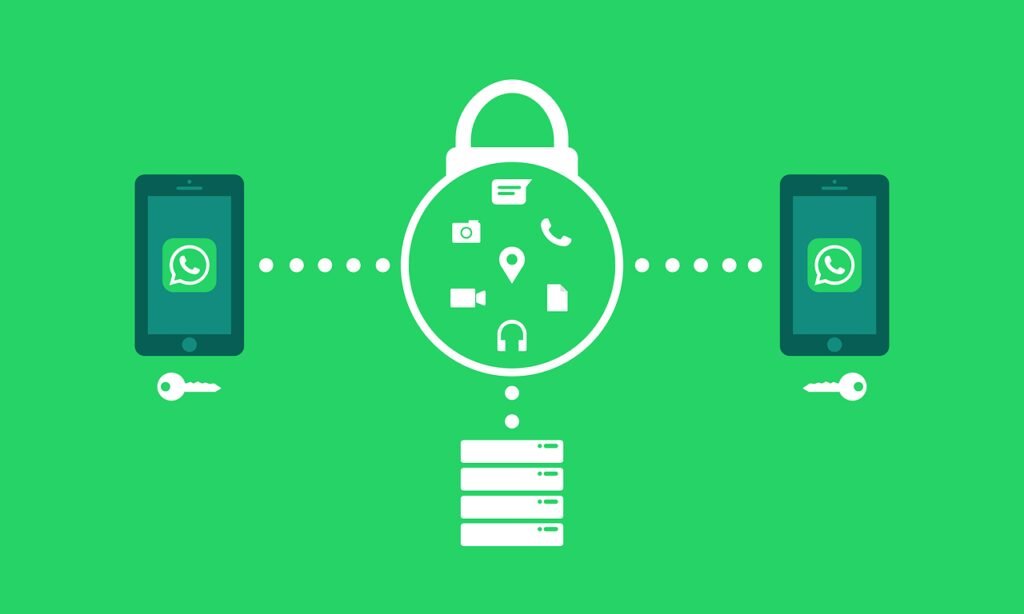
End-to-end encryption (E2EE) is a critical feature in modern messaging apps, designed to ensure that only the intended recipients can read the messages. Popular messaging platforms like WhatsApp and Signal employ E2EE to protect user privacy and maintain the confidentiality of communications.
The process of E2EE can be broken down into several steps:
1. When a user sends a message, the app generates a pair of cryptographic keys: a public key and a private key.
2. The public key is shared with the recipient, while the private key remains on the sender’s device.
3. The message is encrypted using the recipient’s public key before it leaves the sender’s device.
4. Upon arrival, the recipient’s app uses its private key to decrypt the message.
5. This ensures that only the recipient can read the message, as no other party possesses the private key required for decryption.
The benefits of using end-to-end encryption include:
- Enhanced privacy: Only the communicating users can read the messages.
- Data security: Messages are protected from eavesdropping and interception.
- Trust: Users can communicate without worrying about unauthorized access.
- Compliance: E2EE helps comply with data protection regulations.
Encrypting Data at Rest and in Transit
Encrypting data at rest and in transit addresses different security challenges, providing comprehensive data protection.
Data at rest refers to information that is stored on physical or virtual storage systems, such as databases, file systems, and backups. Encrypting data at rest ensures that even if unauthorized entities gain physical access to storage devices, they cannot easily read or use the information without the corresponding decryption keys. For example, sensitive customer details on a company’s servers can be safeguarded by encrypting the database where this data is stored.
Here is an example of encrypting data at rest using the AES (Advanced Encryption Standard) algorithm in Python:
from Crypto.Cipher import AES
import base64
def encrypt_data(data, key):
cipher = AES.new(key, AES.MODE_EAX)
nonce = cipher.nonce
ciphertext, tag = cipher.encrypt_and_digest(data.encode('utf-8'))
return base64.b64encode(nonce + ciphertext).decode('utf-8')
key = b'Sixteen byte key'
data = 'Sensitive data to encrypt'
encrypted_data = encrypt_data(data, key)
print(f'Encrypted data: {encrypted_data}')
Data in transit, on the other hand, refers to information being transferred between systems, such as through networks or between devices and servers. Encrypting data in transit is essential to prevent interception and unauthorized access during the transfer process. Secure communication protocols like HTTPS, which employ SSL/TLS encryption, are commonly used to protect data in transit.
Here is an example of using Python’s `ssl` module to establish a secure connection for data transmission:
import socket
import ssl
hostname = 'www.example.com'
context = ssl.create_default_context()
with socket.create_connection((hostname, 443)) as sock:
with context.wrap_socket(sock, server_hostname=hostname) as ssock:
print(f'Secure connection established with {hostname}')
ssock.sendall(b'GET / HTTP/1.1\r\nHost: www.example.com\r\n\r\n')
print(ssock.recv(1024).decode('utf-8'))
encrypting data at rest and in transit is indispensable for maintaining data security in modern applications. By implementing robust encryption practices, organizations can protect sensitive information from unauthorized access and ensure secure communication channels.
Challenges and Limitations of Encryption
Encryption is a crucial technology for safeguarding our digital data. However, it comes with its own set of challenges and limitations.
Key Management Issues
One of the primary challenges in encryption is key management. Here are some common problems:
- Key Storage: Storing keys securely is essential. If keys are compromised, the encrypted data is at risk. 🗝️
- Key Distribution: Safely distributing keys to the right users without interception is tricky. 📬
- Key Rotation: Regularly updating keys to prevent unauthorized access can be complex and time-consuming. ⏳
Performance Impacts
Encryption can have significant performance impacts on systems. Here are a few examples:
- Slower Processing: Encrypting and decrypting data requires computational power, which can slow down systems. 🖥️
- Increased Latency: Encrypted communications can experience delays, affecting real-time applications like video calls. 📞
- Resource Consumption: Encryption uses more memory and processing power, which can be a limitation for devices with limited resources. 📱
Vulnerabilities and Attacks
Despite its strengths, encryption is not impervious to vulnerabilities and attacks. Some common ones include:
- Brute Force Attacks: Attackers try all possible keys until they find the correct one, which can be time-consuming but possible with enough resources. 🔓
- Man-in-the-Middle Attacks: In these attacks, an attacker intercepts and possibly alters the communication between two parties. 👥
- Side-Channel Attacks: These attacks exploit physical characteristics of the encryption process, like timing or power consumption, to extract keys. 🔌
Let’s look at a couple of real-life examples to understand these challenges better:
- During the 2018 Facebook Data Breach, attackers exploited vulnerabilities to access encrypted data. 🔐
- In 2013, the NSA was reportedly able to access encrypted communications due to weaknesses in the encryption algorithms. 🕵️♂️
Encryption technology is constantly evolving, and as we step into the future, it’s exciting to see what advancements lie ahead. In this blog post, we’ll explore the future of encryption in simple terms, with some fun elements like emojis, tables, and real-life examples to keep things engaging.
Future of Encryption Technology
The future of encryption technology is incredibly promising. With advancements like quantum cryptography and post-quantum encryption algorithms, our data will be more secure than ever before.
Quantum Cryptography: The Next Big Thing 🌟

Quantum cryptography is poised to revolutionize the world of encryption. Unlike traditional methods that rely on complex algorithms, quantum cryptography uses the principles of quantum mechanics to secure information. This makes it virtually impossible for hackers to intercept or tamper with data. Imagine a secret message that self-destructs if someone tries to eavesdrop! That’s the power of quantum cryptography.
Post-Quantum Encryption Algorithms 🚀
With the rise of quantum computers, traditional encryption methods may become obsolete. Enter post-quantum encryption algorithms. These are designed to be resistant to attacks from quantum computers. Here’s a simple table to compare traditional and post-quantum encryption:
| Feature | Traditional Encryption | Post-Quantum Encryption |
|---|---|---|
| Security | High (for now) | Ultra High |
| Algorithm Complexity | Moderate | Very Complex |
| Susceptible to Quantum Attacks | Yes | No |
Trends and Predictions 🔮
Looking ahead, several trends are shaping the future of encryption technology:
- Increased Adoption of Quantum Cryptography: Governments and large corporations are expected to be early adopters.
- Development of Hybrid Systems: Combining traditional and quantum encryption for enhanced security.
- Focus on User-Friendly Solutions: Making advanced encryption accessible to the general public.
Real-life Example: Imagine you’re shopping online, and your payment information is encrypted using post-quantum algorithms. Even if a hacker uses a quantum computer, your data remains secure. That’s the future we’re heading towards!
Stay tuned for more exciting developments in this field! 🔐
FAQs
What is the difference between symmetric and asymmetric encryption?
Symmetric encryption uses the same key for both encryption and decryption, while asymmetric encryption uses a pair of keys (a public key and a private key) for encryption and decryption.
What is a cryptographic key?
A cryptographic key is a string of characters used in the encryption and decryption process. It determines the output of the encryption algorithm and is essential for maintaining data security.
Why is AES considered secure?
AES (Advanced Encryption Standard) is considered secure due to its robust algorithm and the fact that it uses key lengths of 128, 192, or 256 bits, making it highly resistant to brute-force attacks.
How does RSA encryption work?
RSA (Rivest-Shamir-Adleman) encryption works by using a pair of keys: a public key for encryption and a private key for decryption. It relies on the mathematical properties of large prime numbers to secure data.
What are hash functions and how are they used in encryption?
Hash functions take an input (or message) and return a fixed-size string of bytes. They are used to ensure data integrity by generating a unique hash value for the input data, which can be checked to detect any changes.
What is quantum cryptography and why is it important?
Quantum cryptography leverages the principles of quantum mechanics to create secure communication channels. It is important because it offers the potential for unbreakable encryption, which is essential in the face of emerging threats from quantum computing.
What are post-quantum encryption algorithms?
Post-quantum encryption algorithms are cryptographic algorithms designed to be secure against the potential threats posed by quantum computers, which could break current encryption methods.
What are the potential impacts of encryption on system performance?
Encryption can impact system performance due to the computational overhead required for encrypting and decrypting data, which can lead to increased processing time and resource usage.







