Imagine you’re trying to find a friend’s house in a massive city without any street signs or maps. You’d be lost, right? That’s pretty much what the internet would be like without DNS, or the Domain Name System. It’s the unsung hero that keeps everything running smoothly behind the scenes. Every time you type in a website like “example.com” into your browser, DNS steps in to translate that friendly name into a numerical address that computers can understand. Without it, we’d all be memorizing long strings of numbers just to check our email or watch a video.
In this page, we’ll break down everything you need to know about DNS in simple, everyday language. We’ll cover what DNS is, how it’s structured, the journey of a typical query, and even some tricky parts when making changes to it. By the end, you’ll feel like a pro on this essential internet technology. Let’s get started!
Table of Contents
What is DNS and Why Does It Matter?
At its core, DNS stands for Domain Name System. It’s like the phone book of the internet. Back in the day, phone books listed names next to phone numbers so you didn’t have to remember digits for everyone. Similarly, DNS connects easy-to-remember domain names (like “google.com”) to the actual IP addresses (like “142.250.31.14”) that machines use to communicate.
Why do we need this? Computers speak in numbers—specifically, IP addresses, which are unique identifiers for devices on a network. But humans are terrible at remembering numbers. Can you imagine typing “172.217.12.174” every time you want to search something? No thanks! DNS makes the web user-friendly by handling this translation invisibly.
Here’s a quick example: When you visit a site, your device doesn’t know where “amazon.com” is located. It asks the DNS system, which hunts down the right IP address and sends it back. This happens in milliseconds, so you don’t even notice. But if DNS goes down—like in major outages—it can feel like the whole internet breaks. Remember the 2021 Facebook outage? Part of that was tied to DNS issues, leaving billions unable to access services.
DNS isn’t just about websites; it’s used for email routing, app connections, and more. It’s decentralized, meaning no single entity controls it all, which makes it resilient but also a bit complex. That’s why understanding its layers is key.
To give you a sense of scale, billions of DNS queries happen every day. Popular providers handle trillions monthly! It’s truly the backbone holding the digital world together.
The DNS Hierarchy: A Layered Structure
One of the coolest things about DNS is its hierarchical setup. It’s not a flat list; it’s organized like a family tree, with levels building on each other. This design keeps things efficient and scalable for the billions of domains out there. Let’s break it down into the main layers.
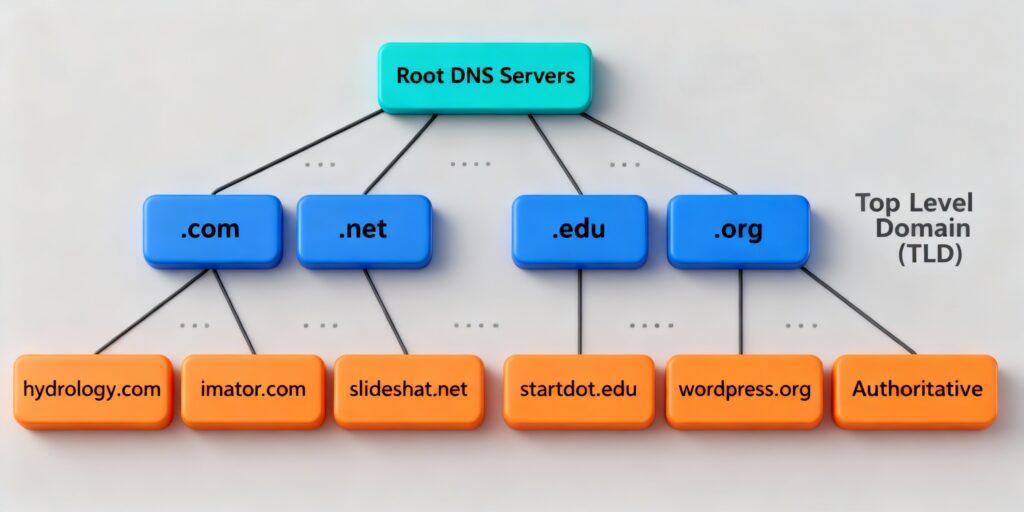
First, at the top, we have the root name servers. These are the starting point for any DNS lookup. There are only 13 logical root name servers worldwide, labeled from A to M (like a.root-servers.net). But don’t let that small number fool you—each one is backed by hundreds of physical servers spread across the globe. Thanks to a technology called anycast, your query gets routed to the nearest one, making it super fast and reliable.
The root servers don’t know the IP for every site. Instead, they point to the next level: the top-level domain (TLD) name servers. TLDs are the endings of domains, like .com, .org, or .net. There are generic TLDs (gTLDs) like .com, country-code TLDs (ccTLDs) like .uk for the United Kingdom, and even newer ones like .app or .blog.
Here’s a table to illustrate some common TLD types with examples:
| TLD Type | Description | Examples |
|---|---|---|
| Generic TLD (gTLD) | General-purpose domains open to all | .com, .org, .net, .info |
| Country-Code TLD (ccTLD) | Tied to specific countries | .in(India), .us (USA), .ca (Canada), .de (Germany), .jp (Japan) |
| Sponsored TLD (sTLD) | Managed by specific organizations | .edu (education), .gov (government), .mil (military) |
| New gTLDs | Modern extensions for niches | .app, .blog, .shop, .tech |
The TLD servers know where to find the servers for domains under them. For instance, the .com TLD server holds info on where to ask about “google.com” or “amazon.com”.
Finally, at the bottom are the authoritative name servers for specific domains. These are the bosses—they hold the actual records, like the IP address for the site. When you buy a domain from a registrar (like GoDaddy), they often provide default authoritative servers, but you can switch to ones from cloud providers like AWS Route 53 or Cloudflare for better performance.
This tree-like structure makes DNS decentralized. No single failure can take down the whole system because responsibilities are distributed. It’s robust against attacks and scales as the internet grows. Imagine if everything was in one database—it’d be a bottleneck!
For an analogy, think of finding a book in a huge library. The root is the front desk directing you to the right section (TLD), which then points to the shelf (authoritative server), where you find the book (IP address).
Types of DNS Servers: Who’s Who in the System
Now that we’ve got the hierarchy, let’s talk about the players involved. DNS servers come in different flavors, each with a job.
- Recursive Resolvers (or just resolvers): These are the workhorses. When your device needs an IP, it asks a resolver, often provided by your internet service provider (ISP). Popular public ones include Google’s 8.8.8.8 or Cloudflare’s 1.1.1.1. They “resolve” the query by chasing down answers through the hierarchy if not cached.
- Authoritative Name Servers: As mentioned, these hold the definitive info for a domain. They’re not guessing—they’re the source of truth. For example, Google’s own servers are authoritative for google.com.
- Root and TLD Servers: These are specialized authoritative servers at higher levels, directing traffic downward.
There’s also caching involved at every step to speed things up. Resolvers remember answers for a while, so repeat queries are instant.
Example: If you’re on a home network, your router might act as a mini resolver, caching common sites to avoid bothering upstream servers.
If you’re curious about testing this, here’s a simple coding example in Python to query a domain’s IP (no need for extra libraries—just built-in socket):
import socket
domain = "example.com"
ip_address = socket.gethostbyname(domain)
print(f"The IP address for {domain} is {ip_address}")Run this, and it’ll spit out something like “93.184.216.34”. This uses your system’s DNS resolver under the hood.
How a DNS Query Works: Step-by-Step Journey
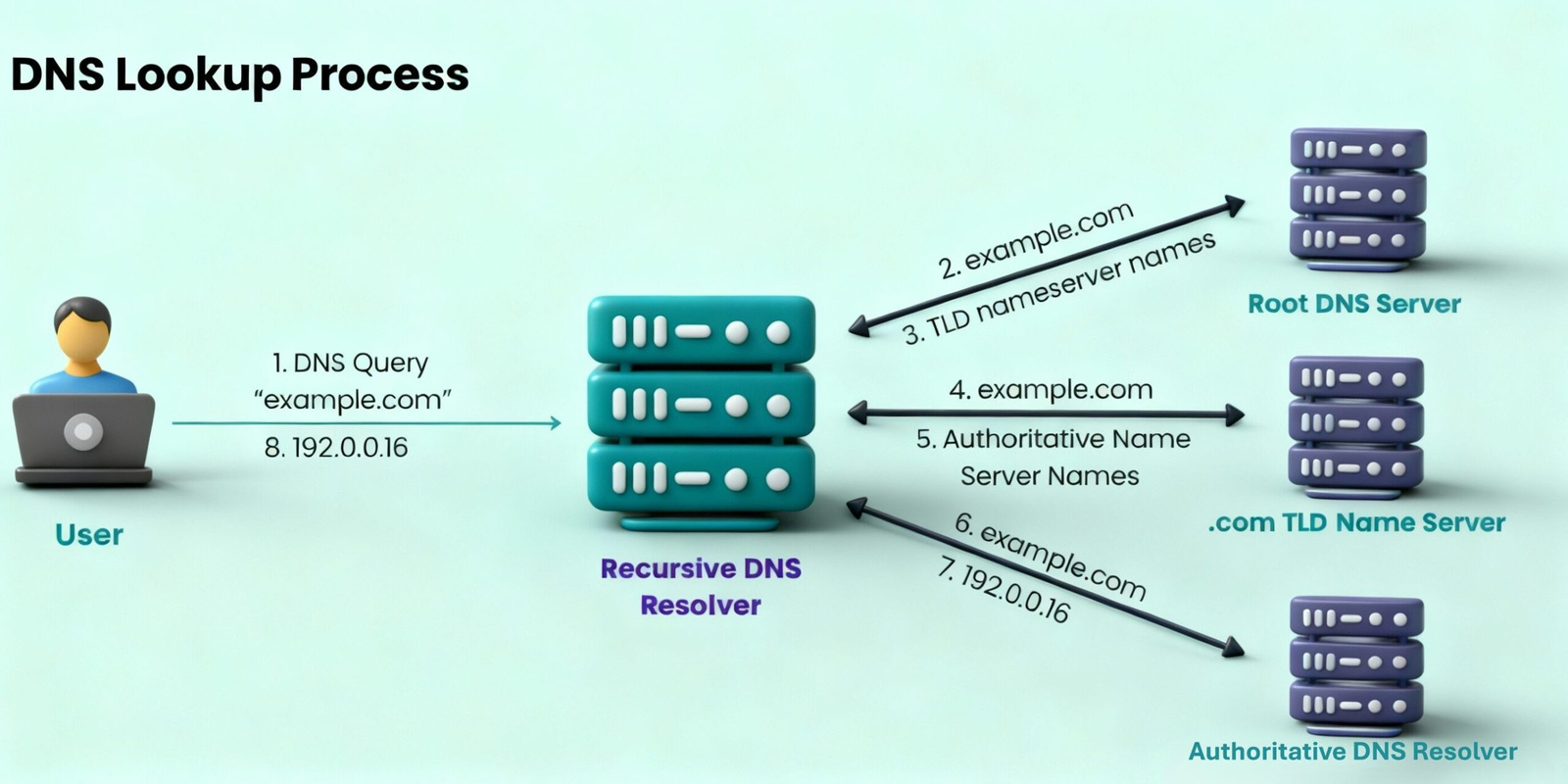
Alright, let’s follow a real DNS query from start to finish. This is where the magic happens. Suppose you type “google.com” into your browser. Here’s what unfolds behind the curtain:
- Browser Cache Check: Your browser first peeks at its own cache. If it remembers the IP from a recent visit, it uses that. No need to ask anyone else.
- Operating System Cache: If the browser draws a blank, it asks your computer’s OS (like Windows or macOS), which has its own cache. Still no? Time to escalate.
- Resolver Query: The OS contacts the configured DNS resolver (e.g., your ISP’s or 8.8.8.8). The resolver checks its cache first.
- Root Server Consultation: If uncached, the resolver asks a root name server. The root says, “For .com domains, talk to these TLD servers” and provides their IPs. (Pro tip: Resolvers often cache popular TLDs like .com to skip this step most times.)
- TLD Server Query: The resolver then pings the .com TLD server, asking, “Where are the authoritative servers for google.com?” The TLD responds with a list, like “ns1.google.com”.
- Authoritative Server Request: Finally, the resolver asks Google’s authoritative server, “What’s the IP for google.com?” It gets the answer, say “142.250.31.14”.
- Response Propagation: The resolver sends the IP back to your OS, which passes it to the browser. Now, your browser can connect directly to Google’s server.
This whole process, called a recursive query, usually takes under a second. But if caches are hit, it’s even faster—often instant.
For variety, consider a subdomain like “mail.google.com”. The authoritative server might point to another server or directly give a different IP.
Caching plays a huge role here. Each record has a Time to Live (TTL), like 300 seconds (5 minutes), telling how long to cache it. Short TTLs mean fresher data but more queries; long ones reduce load but risk stale info.
DNS Records: The Building Blocks
While we’re on queries, let’s touch on what authoritative servers actually store: DNS records. These are like entries in a database.
Common types include:
- A Record: Maps domain to IPv4 address (e.g., example.com -> 93.184.216.34).
- AAAA Record: Same but for IPv6 (longer addresses for the future internet).
- CNAME Record: Aliases one domain to another (e.g., www.example.com -> example.com).
- MX Record: For email servers (points to mail handlers).
- TXT Record: Text info, often for verification or SPF to fight spam.
When you update a domain (say, changing hosting), you’re editing these on the authoritative server.
Example: If you’re setting up a website, you might add an A record via your provider’s panel. Tools like dig (on Linux/Mac) let you query them:
dig example.comThis outputs the IP, TTL, and more.
Challenges When Updating DNS Records
Updating DNS isn’t always smooth, especially for busy sites. The main culprit? DNS propagation—the time it takes for changes to spread worldwide.
Why slow? TTLs! If a record has a 24-hour TTL, resolvers might hold the old IP that long. Plus, some rogue resolvers ignore TTLs altogether.
For a live system with high traffic, this can cause downtime. Imagine switching servers—some users get the new IP, others the old, leading to errors.
Best practices to minimize risk:
- Lower TTL in Advance: Days before the change, set the TTL to something short, like 60 seconds. This ensures when you update, the change propagates quickly.
- Keep Old Setup Running: After updating, don’t shut down the old server immediately. Monitor traffic and wait until it drops low, accounting for non-compliant resolvers.
- Test with Tools: Use sites like dnschecker.org to see propagation status globally.
Example: A company migrating to a new cloud provider reduces TTL from 86400 seconds (1 day) to 300. They update the A record, then watch logs. It might take hours or days for full switchover.
This patience prevents user frustration and lost business.
Advanced Insights: Caching, Security, and Beyond
To deepen your understanding, let’s explore caching more. Caches exist at multiple levels: browser, OS, resolver, even ISPs. This hierarchy reduces root queries dramatically—most are handled locally.
But caching has downsides, like poisoning attacks where hackers insert fake records. That’s why DNSSEC (DNS Security Extensions) adds digital signatures to verify authenticity.
Another trend: DNS over HTTPS (DoH) encrypts queries for privacy, preventing snooping by ISPs.
For developers, integrating DNS in apps might involve libraries like Python’s dnspython for custom resolutions.
import dns.resolver
resolver = dns.resolver.Resolver()
answers = resolver.resolve('example.com', 'A')
for rdata in answers:
print(f"IP: {rdata.address}")This queries directly, bypassing system cache.
Globally, DNS evolves with the internet. With IoT devices exploding, efficient DNS is crucial.
WrapUP
We’ve covered a lot—from DNS basics as the internet’s directory to its hierarchical layers, query journeys, and update pitfalls. It’s a system that’s both simple in concept and ingeniously complex in execution, ensuring the web stays accessible and robust.
Remember, DNS turns names into numbers, powering everything online. Next time you load a page seamlessly, give a nod to this backbone.
Thanks for reading! I hope this cleared up how DNS works. Want to learn more? Don’t miss our breakdown of DNS vs DHCP.
FAQs
What exactly is DNS, and do I really need to care about it?
DNS is basically the internet’s address book. It turns easy names like “netflix.com” into the secret numbers (called IP addresses) that computers use to find websites. You don’t need to think about it daily—it’s like your car’s engine; it just works. But knowing a bit helps if you’re troubleshooting slow loading or setting up a site. Without DNS, you’d be punching in numbers to browse, which would suck!
How does DNS actually find a website’s address?
Picture it like asking for directions in a big city. When you type a site, your computer checks its own memory first. No luck? It asks a helper (the resolver) to climb the “address ladder”: starting at the top bosses (root servers), then the neighborhood guides (TLD servers, like for .com), and finally the exact house owner (authoritative server) who gives the real address. The whole trip takes less than a blink, thanks to shortcuts like caching.
What’s the difference between all these DNS servers?
There are a few team players:
Resolvers: The friendly scouts who do the legwork for you (like your ISP’s or Google’s free one at 8.8.8.8).
Root servers: The big bosses at the top—only 13 main ones, but they’re everywhere via smart routing.
TLD servers: Middle managers for endings like .com or .uk.
Authoritative servers: The experts holding the final answers for a specific site.
It’s a relay race, not one person doing it all, which keeps things speedy and tough to break.
Why does changing a website’s DNS take so long to show up everywhere?
Blame the “expiration date” on each address entry, called TTL (time to live). It’s like a sticker saying how long helpers can trust the old info—could be minutes or days. Some helpers ignore it, too, so changes “propagate” slowly across the world. Pro tip: Shrink that TTL way down before you switch, and keep your old setup running a bit longer to catch stragglers.
What are DNS records, and why would I mess with them?
Think of records as sticky notes on your site’s file with details like its address (A record for basic IPs), email setup (MX), or shortcuts (CNAME for “www.yoursite.com” pointing to the main one). You tweak them when moving hosts or adding email. It’s like updating your contact card—easy in your domain dashboard, but test it to avoid mix-ups.
Can DNS get hacked or cause big problems?
Yep, it’s a target because it’s everywhere. Hackers might swap addresses to fake sites (called poisoning), or overload it in attacks. But fixes like DNSSEC (fancy locks on records) help. Big outages, like when a provider glitches, can knock out chunks of the web—remember times when nothing loaded? That’s often DNS hiccups.
Should I use a public DNS like Google’s or Cloudflare’s?
Totally! Your ISP’s default works fine, but public ones (8.8.8.8 for Google, 1.1.1.1 for Cloudflare) can be faster, more private, or block junk. Switch in your device settings if sites feel sluggish. Just pick one that’s reliable—no magic, but it can smooth your surfing.
How does DNS handle all the world’s websites without crashing?
It’s built smart: spread out like a web (ironic, right?), with caches everywhere to avoid asking the top dogs constantly. Billions of lookups daily? No sweat, because most are quick local grabs. As the internet grows, cloud pros like AWS keep it humming.
Is there a way to check DNS stuff myself without being a tech whiz?
Sure! Tools like “nslookup” in your command prompt (type nslookup google.com) show the address hunt. Or websites like whatsmyip.org let you peek at records. For fun, try that simple Python snippet from the article to grab an IP—it’s like peeking behind the curtain.